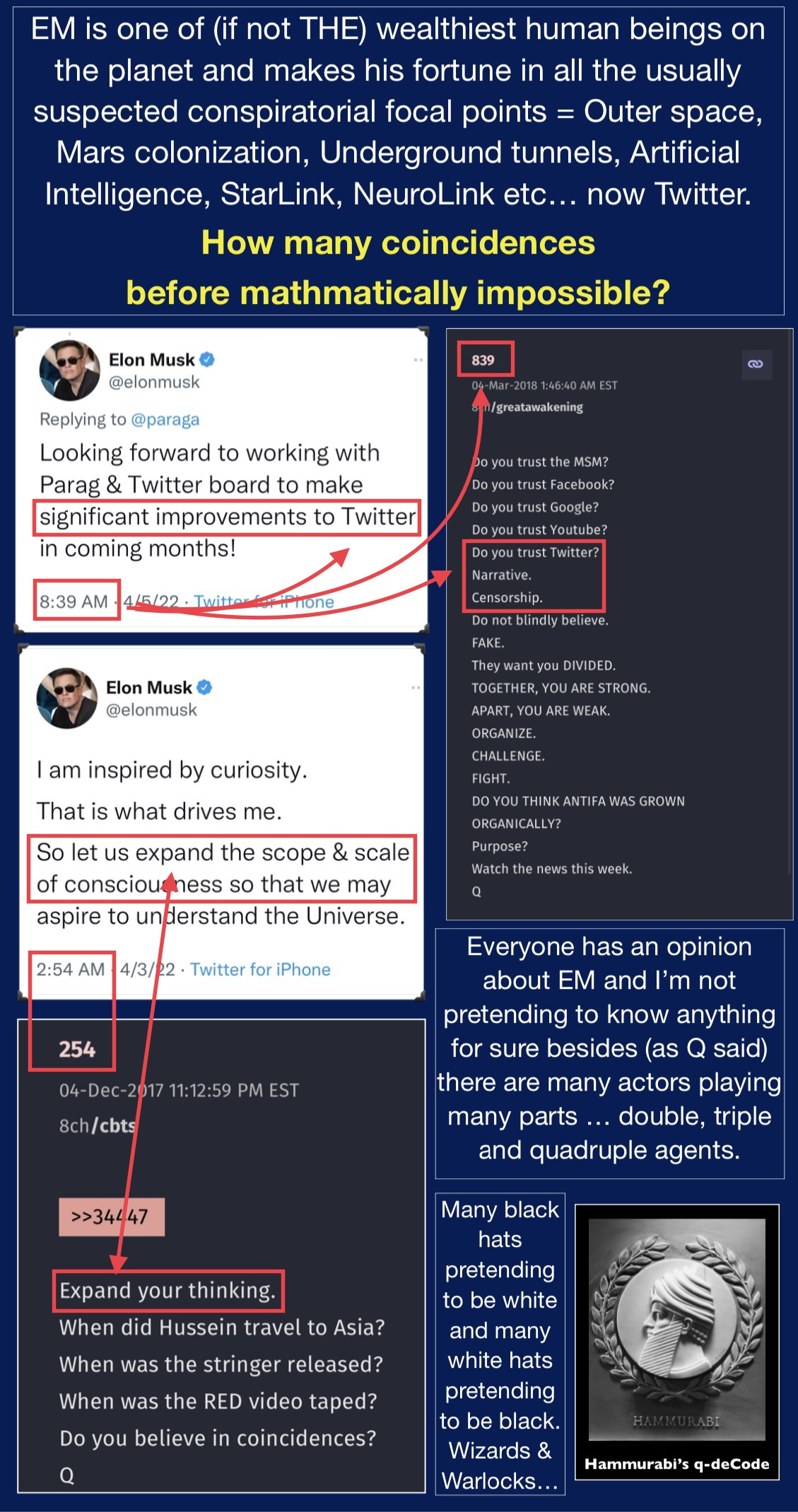
Is an Ancient Space Ark at Lake Vostok heating up Antarctica?
WRITTEN BY DR MICHAEL SALLA
On March 18, news emerged of a heatwave in East Antarctica, the epicenter of which was the Vostok region that sits atop a mysterious lake two miles under the ice sheet. Scientists are baffled by the heat surge of more than 70 degrees above average temperatures and are seeking answers. A likely explanation comes from two sources who say an ancient ark is buried under the ice sheet in the Vostok region, and its activation is heating up East Antarctica.
The Washington Post was the first to reveal the heatwave in East Antarctica. In a story titled “It’s 70 degrees warmer than normal in eastern Antarctica. Scientists are flabbergasted”, this is what was reported:
The average high temperature in Vostok — at the center of the eastern ice sheet — is around minus-63 (minus-53 Celsius) in March. But on Friday, the temperature leaped to zero (minus-17.7 Celsius), the warmest it’s been there during March since record keeping began 65 years ago. It broke the previous monthly record by a staggering 27 degrees (15 Celsius).
Antarctic scientists are baffled by the heatwave in late March since “Antarctica is losing about 25 minutes of sunlight each day,” according to what they told the Washington Post. Meteorologists reported a “heat dome” over East Antarctica and said, “[T]his is not something we’ve seen before.” Significantly, the Washington Post reports that there has been notable melting of the ice sheet in the region.
This takes me to the discovery of a large magnetic anomaly at one end of Lake Vostok as first reported in The Antarctic Sun on February 4, 2001. The anomaly’s size was 65 by 46 miles (105 by 75 km) according to scientific measurements. Veteran NASA researchers Richard Hoagland and Mike Bara soon after proposed the anomaly may in fact be a buried city.
Ground penetrating radar image of lake under Vostok base with magnetic anomaly
Since 2001, there have been multiple sources that claim they have visited or been briefed about an ancient city or large alien motherships buried under the ice sheets either at Lake Vostok or other areas in Antarctica.
What could be driving the heatwave and heat dome over East Antarctica? Is it connected to the magnetic anomaly at Lake Vostok two miles under the ice sheet?
While meteorologists struggle to give a conventional explanation, they admit to being baffled by what is happening. There is another non-conventional explanation for what is driving the heatwave in east Antarctica — a space ark buried under the Vostok region that has begun activating!
On March 29, I was contacted by Jean Charles Moyen, who is a French contactee and secret space program insider that I’ve interviewed previously for Exopolitics Today. Jean Charles is a filmmaker working on the sequel to his first “fiction based on fact” movie, South Shore Origin. In his email message, Jean Charles reported a teleportation experience first to Ireland, where he met Elena Danaan. He next went with her to a Galactic Federation of Worlds mothership in Earth orbit, and finally traveled to Lake Vostok, Antarctica.
Here is how he summarized it all:
Monday, March 28, 3:33 a.m. Here is what I experienced!!!
Last night I was working on South Shore Origin 2, I got up to lie down on the couch in my office because my head was spinning (too much computer probably) and all of a sudden I felt myself go into the couch and I passed out.
When I opened my eyes, I found myself in the path of the other time in Ireland, and I heard, remember, remember…and I saw the same scene again but until the end without interruption !!! Elena was holding my hand and said, I’m going to introduce you to the family and then I saw the next part…
I felt tingling all over my body exactly the same sensation as when you sleep on your arm and the blood comes back in it. You know that scary tingling sensation. Suddenly I was up in a ship, in a big control room with a huge view of space and Elena was next to me and she said to me, you saw, it’s beautiful the view, I like to come here, it relaxes me to see the earth like this, it calms me. And there in the middle stood Melanie [Jean Charles’s wife] in a silver tight suit! Who said you were surprised to see me here, honey !!!! Elena and I have known each other for a long time and we are friends, but I’ll let you continue your visit and she teleported herself!!!!
And then someone came up behind us, I instantly felt his energy, and the hairs on my arms stood up as if electrified. I turned around and saw a man in a uniform with shoulder pads, almond shaped eyes of a very luminous lagoon color and beautiful blond hair that looked like an angel as in the Bible, there was no flaw on his face, it was disturbing to see the perfection of his features. He smiled at me and I heard in my mind relax, my friend you know who I am and he came closer and put his fingers in a triangular shape on my forehead and temples and I found myself surrounded by translucent blue ice, I said: where are we? He told me under Antarctica, precisely under the lake Vostok, where there is an ark.
And I turned around and Elena was there in a tight-fitting suit that pulsed a kind of bluish energy with heat to regulate your temperature, I had no suit but I had the same bluish energy around me. And I said but why are we here…and I heard, because you are all the keys to the awakening of humanity.
And suddenly I felt myself being pulled backwards as if I was falling into a hole and I woke up with a start with my heart pounding in my chest it was precisely 3:33.
After receiving Jean Charles’s startling information, I contacted Elena Danaan to see if she or Thor Han had any info about Lake Vostok and what Jean Charles had experienced. The response from Thor Han to my inquiry was stunning, and gave critical information that explains the heatwave and melting ice in the Vostok region:
The civilization who left technology under the melting ice of Antarctica wasn’t from Nataru [Milky Way Galaxy]. There were ancient times when the climate of this planet was different, when the magnetic poles were located in a different place. The land was green and fertile and the climate was warm, in the land you call now Antarctica. An important colony was settled there. They were of the Pa-Taal. They lived in peace and prosperity. It was a great civilization, told about in your ancient tales as a lost continent. In truth, it was never lost but forgotten, under the ice, for a reason. They left gifts, large crafts and structures in the subterranean web of heated caverns. The structures under Lake Vostok were known from a long time by your scientists working in the secret programs. The Earth Alliance knew, and it was the bait to bring financial elites down to Antarctica for the last meeting. They never saw the Arks, they were never taken there. But this is another story. The ark under Vostok Lake is part of a much larger structure of halls and temples. A powerful pyramid generator is also there. None could activate it. Yet.
Thor Han appears to be describing an ancient civilization such as Atlantis, which has long been rumored to be buried under the ice sheets after the last cataclysmic earth changes occurred 11,600 years ago. A book by researchers Rand Flem-Ath and Rose Flem-Ath, Atlantis beneath the Ice: The Fate of the Lost Continent (2012), presents compelling evidence for such a claim.
In addition, Thor Han refers to recent meetings held in Antarctica where the Cabal (aka Deep State leaders) secretly traveled to negotiate with the Earth Alliance and the Galactic Federation about their future. The cabal reneged on whatever deal was reached and continue to cause chaos on Earth as evidenced by current global events.
Thor Han continued his update:
Not only the Earth Alliance and the Nataru Alliance knew about it, but also the enemy. The Ciakahrr stormed and took the place under Vostok, hoping to crack the codes of this technology. They welcomed the humans of the Nazi group, that you call the Fourth Reich, to help decrypting this technology. Were you thinking that they accepted human colonies there in Antarctica for no reason? What do you think they were getting in exchange for technology and weapons? DNA. The Ciakahrrs knew DNA was the key to activate these power structures. But even though they looked into finding the right DNA frequency codes, they never succeeded to activate these structures.
The Intergalactic Confederation has more than one safety lock on these structures, and what comes with DNA is Consciousness. The body envelope and the inhabiting soul need to be of the same frequency, and the person needs to be alive and conscious, and know what to do, how to activate the commands and unlock the portals. You need the knowledge that goes with the tools. You cannot kill someone and only use their DNA sample, because it needs to be inhabited by consciousness. By an original soul part of the Seeders, who have this knowledge. Bodies are also there in stasis, and they were found a long time ago. But their genetic material isn’t enough, because the soul has gone, and awaits to come back.
Now, the ice is melting, to reveal in plain sight the secrets we liberated, for you.
I have earlier reported on my US Army source JP who has traveled to arks on the Moon and under the Atlantic Ocean, where a multinational team drawn from the US, China, and Russia has been researching the ancient arks. JP confirmed that the arks are activated by the DNA of a select number of individuals.
Consequently, it is very plausible that the Draco Reptilians, aka Ciakharr, used the Nazis to get access to human DNA they could use to activate the arks. In addition, JP has revealed that the activating arks are releasing a tremendous amount of heat, quickly warming up the surrounding environment.
In a voice communication received on March 29, Elena confirmed that she had been taken to Lake Vostok with Jean Charles in the early morning of the previous day:
This is now the explanation why I wasn’t allowed to remember this moment because it was meant that Jean Charles remembers. I think it’s a good strategy that they scatter information, not always the same person you know. I find it very good. Then there was a lot of also holographic projection around Jean Charles to show him, make him confident and settled in the project … Melanie was there as well to make him confident, but I was really there and with him, and I remember now, but he was meant to be the one to remember first because as Thor Han always says, remembering is activating. So now we can confirm about Lake Vostok.
Elena’s confirmation shows that the Galactic Federation is now taking at least two individuals to visit the space arks, witness the contents, and report their experiences to the world.
In a follow-up message from Jean Charles on March 29, he explains being taken on a second trip to Lake Vostok earlier in the morning of that day:
This night, I found myself in the same place under Lake Vostok, but this time I was inside a structure. It was the Ark. Everything was purified inside, no screws, nor bolts, nothing. It looked like tungsten but translucent. I was in the center, and in the middle, there was a kind of sphere which turned very luminous. They would have said a ball of bluish plasma which gave off a lot of heat by emitting a crystalline noise and around was laid out in a geometrical form resembling a star … tubes in which there were beings in stasis.
I approached one of the tubes, and when I approached, it reacted by lighting up, as if my presence triggered it. I felt in connection with the material of the vessel. The structure seemed alive. I could see the appearance of the being in the tube, he was tall, and his skin had bluish reflections. He was wearing a kind of midnight blue suit without any seams. There was a symbol on the suit representing a triangle with a constellation inside. And I heard a voice coming out of nowhere saying to me, “you have been chosen,” it was the same sentence that the Mantis [being] had said to me as a child when she put her paws on my shoulder, you remember, during the test of fear with the other children? Many of them had failed except me. Well, it was the same voice. I approached a tube, and it lit up very brightly, and I woke up suddenly and on the alarm clock it was 5:55.
Jean Charles’s information matches what JP said he had encountered during his two trips to the submerged Atlantic space ark. He described a blue ball of liquid (plasma) in one large room, which was a portal to other space arks. In addition, he witnessed many crypt-like structures whose contents were not seen by JP, but he said he was briefed that they radiated friendly energy.
In addition, in an upcoming update from “Oona”, a representative of the 24 Seeder Races (aka Intergalactic Confederation), it will be confirmed that the sleeping giants are starseeds currently incarnated on Earth. Elena plans to soon reveal this fascinating update.
In conclusion, the experiences released by Jean Charles Moyen and Elena Danaan, when combined with the earlier revelations from JP, all suggests that an ancient ark is activating and warming up the Vostok region and the rest of East Antarctica. Furthermore, the ancient ark is almost certainly linked in some way to the large magnetic anomaly discovered at one corner of Lake Vostok back in 2001.
The record temperatures in East Antarctica recently reported by the Washington Post suggest the heating up process caused by the activating ark(s) is unstoppable. It therefore is only a matter of time before the world will be confronted by indisputable physical evidence of an ancient Atlantean civilization buried under Antarctica, and the existence of large space arks buried in Antarctica and other locations around the planet.
What will be even more exciting for the general public and many readers in particular is the revelation that the ‘sleeping giants‘ in the space arks are human starseeds currently living normal lives on Earth. These starseeds are destined to awaken to their DNA or “soul” connection to the hibernating crews of the activating space arks through dreams, visions, and eventually physical travel there as happened with both Jean Charles Moyen and Elena Danaan.
A video version of this article is on YouTube & Rumble
Audio Podcast on Apple, Spotify, or Google
© Michael E. Salla, Ph.D. Copyright Notice
Many thanks to Jean Charles Moyen and Elena Danaan for permission to publish their email communications. Jean Charles Moyen’s movie “South Shore Origin” is available on Vimeo here. Elena Danaan’s website is here.
Note: On April 9 I will be holding my next webinar on “ET Seeders, Space Arks, and the Great Reveal” where I describe the history of space arks and the ‘Seeders’ and why their recent arrival is triggering the arks activation, which in turn will lead to incredible revelations about humanity’s origins and connections to extraterrestrial life. Click here or banner below for more info.
Related Articles/Podcasts
Buried Ukraine space ark in Kherson activates so Russia takes over
Atlantic Space Ark Rescue Mission
Joint US China Mission to Giant ET Space Ark under Atlantic Ocean
Joint US China missions sent to crashed alien spacecraft discovered by Yutu 2
French SSP Insiders Speak Out
20 Years & back with the French Secret Space Program